This is an attempt to provide some basic information about the dreaded heartbleed bug and what you can do, as an individual , in order to follow best practice in order to protect yourself from the bug.
What you will learn:
- The basics of what heartbleed is
- Where it came from
- How you can determine if a website is currently showing signs of the vulnerability
- What resources are known to be affected or were previously affected
- What you can do to protect yourself and your technology as a user
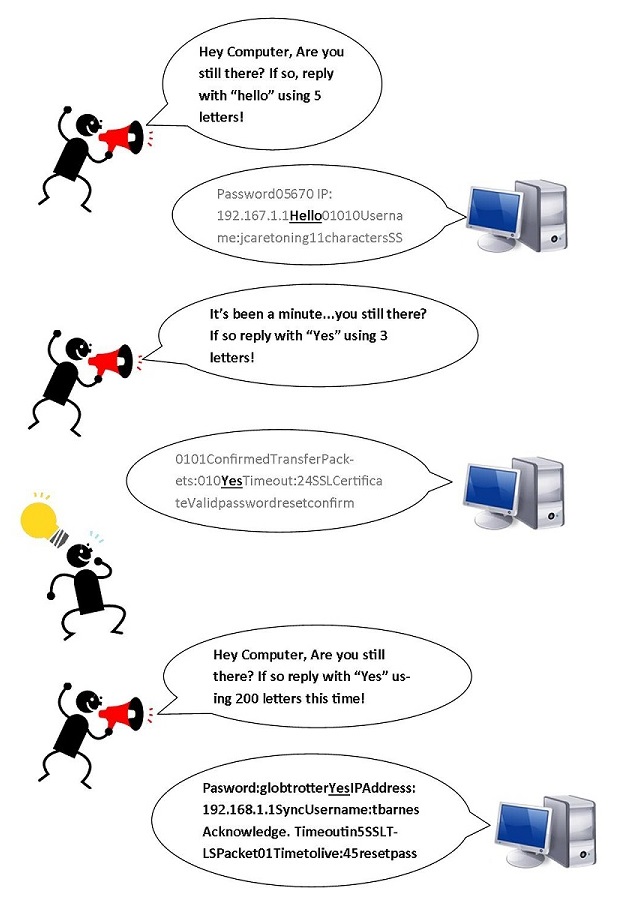
- A very simplistic image showing you how the bug is most commonly exploited
What is it?
First, the Heartbleed bug is not a virus, it’s actually a bug or flaw in the design of Opensource SSL usage of the TLS security protocol. These protocols are often utilized when you go to a website that contains an address such as https://something.com, the “S” in https, stands for SSL or Secure Socket Layer…translation, the traffic is encrypted. This is designed to keep information hidden so that sensitive information, such as passwords, are not discovered. No, this does not mean that all sites that have https in their address are now unsafe to utilize. Most bank and financial institutions have been determined to be safe from the bug.
Where did it come from?
Open SSL is the source of the issue. For those that are technical…The affected versions of OpenSSL are OpenSSL 1.0.1 through 1.0.1f
How can I determine if a website is affected?
Check your website or one that you use often by visiting here to Test Your Site.
What resources were known to be affected?
- Up to 17% of the worlds secure web servers
- Yahoo
- Flickr

- Open SSL Server and Clients
- Web browsers
- Dropbox
- Mobile apps on Android
- Mobile apps on Apple IOS
- Social Networks
- File Sharing Applications
- Cisco home grade routers
- Juniper home grade routers
- Many linux web server platforms
- Akamai Technologies
- Amazon Web Services
- Ars Technica
- Bitbucket
- BrandVerity
- Freenode
- GitHub
- IFTTT
- Internet Archive
- Mojang
- Mumsnet
- PeerJ
- Prezi
- Something Awful
- SoundCloud
- SourceForge
- SparkFun
- Stripe
- Tumblr
- Wattpad
- Wikimedia
- Wunderlist
You get the idea…
What should you do?
You should change your passwords for any website or service that you believe may have been vulnerable or susceptible to the bug. Originally, up to 17% of the worlds web servers were believed to be exposed. At this point, many of those resources have been patched so this would be a good time to follow through with a password change to ensure that, if yours was ever captured, the information would no longer be relevant.
How does it work?
This is a very simplistic example of what’s known as a buffer over-read. Which is one primary method to exploit the heartbleed bug.
Not sure what to do?
If you find that you are concerned about resources that your company utilizes. Feel free to contact us at Superior Solutions and we can work with you to determine if those resources are at risk and how to remove the threat.
If you found any of this information to be useful, Please feel free to share!